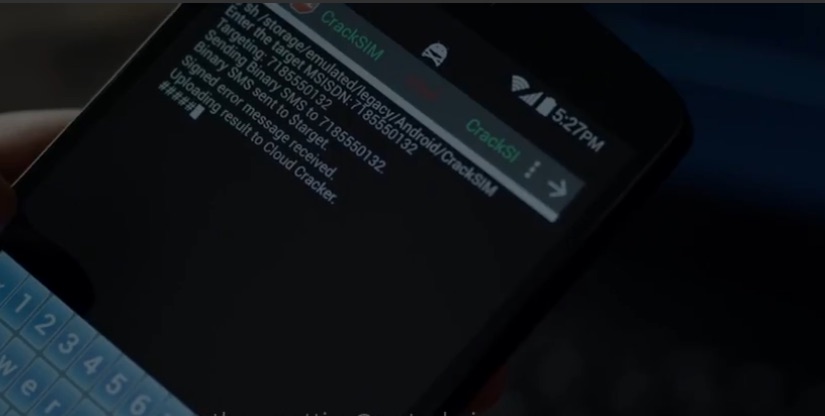
Hacking a smartphone is easy but do you know your phone can be hacked over the air too ?
Hackers look for vulnerabilities in your software that allow them to install their own programs. They'll use these programs to gain root access and/or get your password.
Vulnerabilities are typically code defects that occur in areas where we are dealing with outside data entering the device. Imagine a program that reassembles USB packets. As it gets each packet it copies it into memory somewhere.
What if we could trick it into copying more data than it should? Imagine you have a bucket that can hold a gallon of water. If you pour more than a gallon in what happens? It spills right?
This is called a buffer overflow in computer science terms, and it allows hackers to write data into places they shouldn't. Sometimes that data can be a program or a piece of code that allows them to install their own programs.
It gets complicated quickly but the gist is "If your program is handling outside data it can potentially be exploited"
No comments:
Post a Comment